Everything inline.
Working on Snort_inline 2.8.0.1
The last week I’ve been working on bringing Snort_inline to the Snort 2.8.0.1 level, including it’s IPv6 support. I’m almost ready to commit it to SVN, there are just some issues I need to fix in the inline specific code. The code will get rid of libdnet and use libnet 1.1 for sending reset/reject packets for both IPv4 and IPv6. After committing I will start working on getting the IPv6 features I wrote for NitroSecurity into this tree. This includes more matches, tunnel decoding (including for example the freenet6 tunnel, etc). So stay tuned!
…New Snort_inline TCP window normalization code in SVN
A while ago I wrote about why the TCP window scaling normalization in Snort_inline was broken by design. I also wrote about a new solution I was working on and testing that would be uploaded to SVN soon. I just committed the patch to SVN. What it does is add two new options to stream4:
norm_window: normalize the TCP window (disabled by default). This is to protect Snort_inline from being forced to queue too many packets. max_win_size: maximum size of the scaled TCP window. Packets increasing the window beyond the limit are modified.
…
Matt Jonkman leaves Bleeding Edge
Matt Jonkman is stepping out of the Bleeding Edge project. He announced this here. Apparently Sensory Networks, one of the sponsors of the project, now owns it. It will be interesting to see if they will continue it, and if so, how. Honestly, I’m a bit skeptical, since to my knowledge not many Sensory people are directly involved at this moment. Still I believe Sensory consists of good people. I did a contract job for them about a year ago, and enjoyed working with them.
…Deactivating a group of sensors in Sguil 0.7.0-CVS
Recently a site I was using for my Vuurmuur project became unavailable to me. I had two sensors in that site, one Modsec2sguil sensor and a Snort sensor. Since it became unavailable to me, the sensors were all offline and will stay that way. So I wanted to hide them in Sguil, including the net_name group they belonged to, called ‘utrecht’.
Doing this turned out to be quite simple. The sensors have their own table in the database and one of the fields for a sensor is called ‘active’. I figured deactivating the sensors would do it. Deactivating all sensors from the net_name group ‘utrecht’ is done like this:
…Multiple Snort_inline processes with Vuurmuur
One of the cool things of the Snort_inline project is the support for NFQUEUE. NFQUEUE is the new queuing mechanism to push packets from the kernel to userspace so a userspace program can issue a verdict on it. What makes NFQUEUE cooler than it’s predecessor ip_queue is that it supports multiple queue’s. This means that there can be more than one Snort_inline process inspecting and judging traffic. The challenge is to make sure that each Snort_inline instance sees all traffic belonging to a certain connection so Snort_inline can do stateful inspection on it. Luckily, Vuurmuur makes it very easy.
…GUI part of Vuurmuur traffic shaping done
The GUI part of Vuurmuur’s traffic shaping is done. That means it’s in a usable state. It’s probably rough around the edges, but anyone is invited to give it a try. Below two screens.
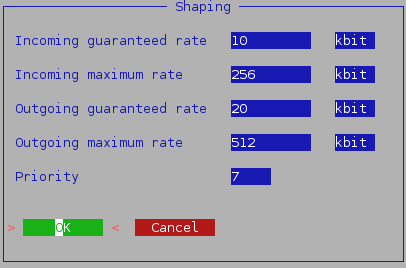
The per rule shaping settings.
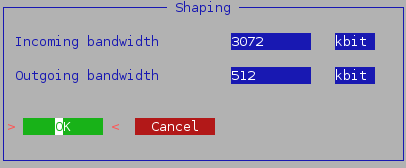
Vuurmuur shape interface settings.
The per interface settings for the shaping.
…Sguil 0.7.0 CVS client on HeX 1.0.1
The last few days I’ve been playing with the HeX live-cd. It boots fine on my Lenovo T60 laptop. So after about a minute a nice graphical interface awaits me. I really love the artwork of this project.
There are many security tools installed, including the Sguil client. This is the 0.6.1 version however. As I have written before, I’m running 0.7.0 CVS here, so I needed the 0.7.0 CVS client. Luckily, it’s easy to install.
…Sguil 0.7-CVS client on Ubuntu Gutsy
Last week I installed Ubuntu Gutsy on my laptop. I did a clean install, which went fine. Of course, I needed the Sguil client on it as well. Gutsy has all the required libraries in it’s repositories. Install the following packages:
tcl8.4 tclx8.4 tcllib tk8.4 iwidgets4
Checking out the Sguil client is easy (make sure you have ‘cvs’ installed):
cvs -d:pserver:anonymous@sguil.cvs.sourceforge.net:/cvsroot/sguil login cvs -d:pserver:anonymous@sguil.cvs.sourceforge.net:/cvsroot/sguil co sguil
After this the client runs fine on my system.
…Libnet 1.1 IPv6 fixes and additions
Libnet is a cool packet crafting tool, used by Snort to send TCP reset packets and ICMP unreachable packets as part of active responses. Libnet 1.1 supports IPv6 which is what I needed for my work. After some reading and testing there were a few problems. First, while possible to send TCP reset packets, the packets didn’t have a correct checksum and debugging this with valgrind showed lots of memory errors. Second, ICMPv6 was only partly implemented. The libnet_build_* functions for it are missing. This is, by the way, quite a common picture. Many libraries and projects have some support for IPv6, but generally incomplete and less well tested.
…ModSecurity rules for Tikiwiki 1.x tiki-graph_formula.php Function Injection Vulnerability
A new vulnerability has been found in Tikiwiki. Read more about it here.
I’ve created the following ModSecurity rule to block it.
SecDefaultAction “log,deny,phase:2,status:403,t:urlDecodeUni,t:lowercase”
SecRule REQUEST_FILENAME “tiki-graph_formula.php” “chain,msg:‘TIKIWIKI tiki-graph_formula.php link inclusion attempt’,severity:2” SecRule ARGS:/^s*[a-z]+$/ “^(ht|f)tps?://”
SecRule REQUEST_FILENAME “tiki-graph_formula.php” “chain,msg:‘TIKIWIKI tiki-graph_formula.php f parameter Function Injection Vulnerability’,severity:2” SecRule ARGS_NAMES “^s*f[.*]$”
Ivan, I hope these rules survive your scrutiny ;-)
Updated at 13:50: The first rule only covered the file inclusion in the title parameter which was what I was seeing in my logs. These rules should cover both the inclusion and the injection.
…