Everything inline.
First (beta) release of modsec2sguil 0.5
I have been writing about getting ModSecurity alerts into Sguil before. Today I can finally release a first public version. It’s pretty crude, but it WorksForMe(tm).
The release can be found here. If you are interested, please try it. There is some documentation in the archive.
…Sguil: renaming a sensor
This might be a no-brainer for some, but today I wanted to rename a sensor in Sguil, and decided to write the steps down.
Preparation
- backup the db
- stop sancp on the sensor
- stop barnyard on the sensor
- stop sensor_agent on the sensor
- stop snort on the sensor
- stop log_packets on the sensor
- stop sguild on the server
Steps on the Sguil server
Update the sensor name in the database.
…Sguil: adding support for ModSecurity alerts, continued
After the successful test with the Perl script to add ModSecurity alerts to Sguil, I have been working on a more robust implementation, also in Perl. Let me first describe the basic setup. The setup works with two scripts. The first places links to event files into a special queue directory. The second reads the links from that directory, parses them and sends the alerts among these events to Sguil. After that, the links are removed.
…ModSecurity: rule for latest Tikiwiki vulnerability
A few days ago a new vulnerability was reported in Tikiwiki 1.9.x, the software I use for the Vuurmuur Wiki. Luckily, the Snort.org Community rules quickly had a rule for detecting the attack. Because I also run ModSecurity on the webserver, i wanted to have protection there as well. This rule should block the attack:
SecFilterSelective POST_PAYLOAD “jhot.php” “log,deny,status:403,msg:‘LOCAL tikiwiki jhot.php attempt’”
Let’s see if I ever get a hit on it. An update for Tikiwiki as been released, so that should fix the issue completely.
…Vuurmuur: connection killing getting shape
The main new feature of the 0.5.72 release of Vuurmuur will be the ability to kill existing connections from vuurmuur_conf. It will use the conntrack tool for this. Below is a screenshot of how it works.
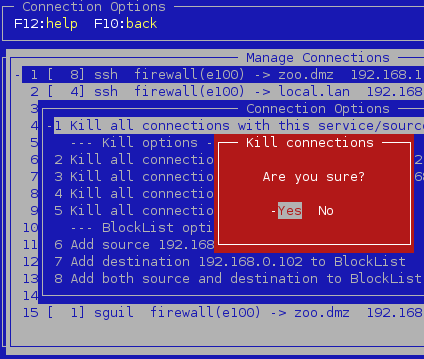
Currently it works only for TCP connections and UDP pseudo connections. From the connection manager IPAdresses can also be added to the blocklist. All existing connections for this IP will be killed on that action. I have yet to extend this to hosts blocked manually.
…Sguil: adding support for ModSecurity alerts
I’m a huge fan of both Sguil and ModSecurity, but sadly the alerts generated by ModSecurity can’t show up in Sguil… or… can they? Well, if it all works out, soon they can!
Today I have hacked together a perl script that emulates barnyard for ModSecurity. It very much in a proof-of-concept phase, but it somewhat works already, at least good enough so i can show this screenshot.
 Nice huh? It is not ready for release yet, but when it is i’ll announce it here. I plan to release it under the GPL. Sguil author Bamm Visscher told me that the next release of Sguil will have support for having barnyard and PADS on the same sensor. By then, i hope that ModSecurity can be added to that list! :-)
Nice huh? It is not ready for release yet, but when it is i’ll announce it here. I plan to release it under the GPL. Sguil author Bamm Visscher told me that the next release of Sguil will have support for having barnyard and PADS on the same sensor. By then, i hope that ModSecurity can be added to that list! :-)
Sguil: detecting ICMP tunnels, continued
A few days ago i wrote about detecting ICMP tunnels. I came to the conclusion that for the two tunnels i tried the properties to detect on were:
- Non-standard average packet size. E.g. 81.81 bytes for the first connection is non-standard.
- Number of bytes in both directions are unequal.
- Average packet size in both directions is unequal.
I believe the third is the most important, because it must mean that 1 is also true and 2 is very likely to be true. If the average packet size is unequal in both directions, one of them should be non-standard. So far i have only seen echo-request and echo-reply being equal in size for pings. Unequal average packet sizes with exactly the same amount of data transfered is very unlikely, so i have ignored that for now.
…Sguil: using advanced queries to get more info on Snort events
Today, David Bianco showed me a way of creating SQL queries that I didn’t even know was possible. This is a technique with which it is possible to query the payload of Snort events in the Sguil database. These payloads are stored by Snort when it alerts and is the payload the actual rule triggered on. David showed a nice example of retrieving url’s for PHP url inclusion attacks.
I have written before about my usage of Mod_Security. I let Mod_Security respond with a 403 Forbidden message. Sadly, the alert generated by Mod_Security can not be displayed in Sguil. As somewhat of a replacement for that, I let Snort alert on the 403 Forbidden messages, so i can see in Sguil that Mod_Security blocked something. The disadvantage of this is that the 403 alert in itself does not contain much info. The sheer number of 403’s makes inspecting every single one with requesting a transcript a bit to much work.
…Sguil: detecting ICMP tunnels
My earlier post about detecting ICMP anomolies was based on dry theory combined with experimenting with the ping command. The last couple of days I have been playing with real ICMP tunnels, to see how detection of those would work. This was easier said than done. Sure, running PingTunnel or itun between two hosts in my LAN worked fine. However, being an inline guy, i have Sancp looking at traffic passing my firewall only. And getting the ICMP tunnels to pass the firewall was the real trick. I won’t bore you with that now, because i intend to look at counter measures later, so i’ll handle that then. For now I will just assume that these ping tunnels will not be blocked by the firewall.
…ModSecurity: rules against comment spam
Lately the wiki of my Vuurmuur project has been receiving quite a lot of comment spam. Although removing the spam manually is boring work, i still don’t really mind the spam, because it enables me to practice with ModSecurity rules to fight it off. So far, the spam seems to be following a pattern, in which the spam is posted by bots, and has the same general layout for longer periods of time. That makes it worthwhile to spend time on creating rules against it. Yesterday a new type of spam emerged on the wiki. The following audit_log is for one of them. I had to slightly edit it for layout reasons.
…