Everything inline.
Suricata Lua scripting flowint access
 A few days ago I wrote about my Emerging Threats sponsored work to support flowvars from Lua scripts in Suricata.
A few days ago I wrote about my Emerging Threats sponsored work to support flowvars from Lua scripts in Suricata.
Today, I updated that support. Flowvar ‘sets’ are now real time. This was needed to fix some issues where a script was invoked multiple times in single rule, which can happen with some buffers, like HTTP headers.
Also, I implemented flowint support. Flowints in Suricata are integers stored in the flow context.
…Suricata: Handling of multiple different SYN/ACKs
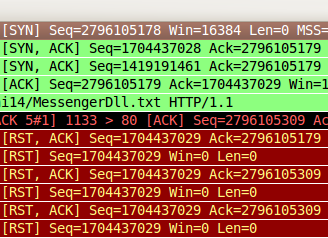 When processing the TCP 3 way handshake (3whs), Suricata’s TCP stream engine will closely follow the setup of a TCP connection to make sure the rest of the session can be tracked and reassembled properly. Retransmissions of SYN/ACKs are silently accepted, unless they are different somehow. If the SEQ or ACK values are different they are considered wrong and events are set. The stream events rules will match on this.
When processing the TCP 3 way handshake (3whs), Suricata’s TCP stream engine will closely follow the setup of a TCP connection to make sure the rest of the session can be tracked and reassembled properly. Retransmissions of SYN/ACKs are silently accepted, unless they are different somehow. If the SEQ or ACK values are different they are considered wrong and events are set. The stream events rules will match on this.
Suricata Lua scripting flowvar access
 Funded by Emerging Threats, I’ve been working on giving the lua scripts access to flowvars.
Funded by Emerging Threats, I’ve been working on giving the lua scripts access to flowvars.
Currently only “flowvars” are done, “flowints” will be next. Please review the code at: https://github.com/inliniac/suricata/tree/dev-lua-flowvar
Pcre based flowvar capturing is done in a post-match fashion. If the rule containing the “capture” matches, the var is stored in the flow.
For lua scripting, this wasn’t what the rule writers wanted. In this case, the flowvars are stored in the flow regardless of a rule match.
…Major Suricata 1.4 update
Major 1.4 update.
…Vuurmuur 0.8rc1 released
 I just released a new Vuurmuur version: 0.8rc1. The first release candidate for the 0.8 series. This release improves IPv6 support a lot. The wizard is now also fully functional. Try “vuurmuur_conf –wizard”.
I just released a new Vuurmuur version: 0.8rc1. The first release candidate for the 0.8 series. This release improves IPv6 support a lot. The wizard is now also fully functional. Try “vuurmuur_conf –wizard”.
- Improved IPv6 support: #115
- Improved Debian packages, switching to nflog as default for logging.
- Fix connection viewer not showing accounting on newer systems. #141
- Amd64 packages for Debian and Ubuntu are now available through the apt server. #83
- Switch from “state” match to “conntrack” match for connection tracking.
- Services now support possible protocols. #63
- Add support for rpfilter match. #137
Get this release from the ftp server: ftp://ftp.vuurmuur.org/releases/0.8rc1/Vuurmuur-0.8rc1.tar.gz
…On Suricata 1.3, 1.4 and "next"
So with 1.4 out the door we have a new stable. However, we’re keeping 1.3 around for a few more months to give everyone the chance to plan updating to 1.4. Of course, we think 1.4 is a lot better than anything we released before, so we do recommend updating as soon as you can.
Continued support for 1.3 means we’ll do more releases to fix critical issues. We’ll probably include trivial fixes of smaller problems. When talking about critical issues I mean crash cases mostly. Anything else will be fixed only in 1.4 and up.
…Suricata 1.4 is out
 About 5 months after 1.3 came out we’ve released 1.4, and we’ve been quite busy. Eric Leblond’s post here has all the stats and graphs. There are three big new features: unix socket, ip reputation and luajit. For each of these the same is true: it’s usesable now, but it’s the potential that we’re most excited about. Over the next months we’ll be extending each of those to be even more useful. We’re very much interested in ideas and feedback.
About 5 months after 1.3 came out we’ve released 1.4, and we’ve been quite busy. Eric Leblond’s post here has all the stats and graphs. There are three big new features: unix socket, ip reputation and luajit. For each of these the same is true: it’s usesable now, but it’s the potential that we’re most excited about. Over the next months we’ll be extending each of those to be even more useful. We’re very much interested in ideas and feedback.
Suricata 1.4.1 is out
First stable release in the 1.4 branch, right in time for the holidays. Enjoy!
…IPv6 Evasions, Scanners and the importance of staying current
Lots of activity on the IPv6 front lately. There was a talk on a conference on bypassing IDS using IPv6 tricks. Also a new scan tool (Topera) claimed to scan a host while staying below the radar of an IDS was released. To start with the latter, even though Suricata doesn’t have a dedicated port scan detector, the tool’s traffic lights up like a Christmas tree. The trick it pulls is to pack a lot of duplicate DST OPTS extension headers in the IPv6 packets. These options are just fillers, the only options they use are the “pad” option. In Suricata we’ve had an event for duplicate DST OPTS headers since 1.3 and the padding only headers generate an event in 1.4. Both alerts will be very noisy, so calling this a stealth attack rather dubious.
…Closing in on Suricata 1.4
 I just made Suricata 1.4rc1 available with some pretty exciting features: unix socket mode and IP reputation.
I just made Suricata 1.4rc1 available with some pretty exciting features: unix socket mode and IP reputation.
Unix socket
First of all, Eric Leblond’s work on the Unix socket was merged. The unix socket work consists of two parts. The unix socket protocol implementation and a new runmode.
The protocol implementation is based on JSON messages over unix socket. Eric will be fully documenting it soon. Currently the commands are limited to shutting down and getting some basic stats. This part isn’t very exciting yet, but the groundwork for many future extensions has been laid.
…